TechLetters #10 - on hacking vaccines process
and more
Welcome to the 10th letter, and the first in 2021.
Éditorial
How would I design a disinformation operation aiming to sow mistrust/distrust to vaccination, specifically for the SARS-CoV-2/Covid-19? Early in 2019, I pointed out that the new situation will contribute to a change in the cybersecurity landscape. In this pandemic, we experience rapid changes. Things happen fast. Even the vaccines were created in under one year.
To sow distrust in vaccines in the West, targeting the vaccine registration process is best. Institutions such as the U.S. F.D.A. or the European E.M.A. are typical bureaucracies. They do not focus on cybersecurity, understandingly so. For them, digital transmissions (i.e. e-mails, document storage, etc) are merely means of work. This is totally fair. But if someone determined, skilled, and with free resources, happen to have an intent to compromise such organisations, it would probably not be that difficult.
This is what happened. European Medicines Agency was hacked. Perhaps it was merely a compromise of an account of a single employee. The end result is a breach. Documents are stolen. They are now released, leaked. These documents describe proprietary vaccine-related information: process, experiments, studies. They contain very hermetic content. Difficult to understand, with plenty of biotech-pharma language. Many numbers inside. Chemical compounds, some of them with amusing names. In the overall, the leaks are difficult to understand, let alone rate by untrained people.
Leaking this and perhaps framing as if something in there was suspicious would be the perfect way to sow distrust in the registration process and in the vaccinations in general.
This is exactly what happened. Participants of some communities (forums…) already try to spin the discussions, and say things along the lines as if something was hidden from the public. Trying to allege (misinterpreting the leaked data?) that the vaccine efficacy is supposedly different from the numbers mentioned to the public. There you go. Your disinformation campaign is on track, it is happening.
The question remains about the source of this, as well as the intent. Specifically, who has an interest in boosting the anti-vaxxer movement in the West? Who would find the interest in compromising the vaccine process? Who would prefer so that the covid19 response in the West encounters obstacles?
This is not a joke. We speak about a broad, emergency medical situation with direct consequences to local and global healthcare systems, and health in general. Humanitarian significance cannot be overlooked. This is a precedent.
Security
Vaccine data leak. European Medicines Agency confirms a #COVID19 vaccine data leak. Attackers manipulated some of the leaked content, maybe to undermine trust in vaccines. "despite this urgency, there has been consensus not to compromise the high-quality standards". It appears as if someone did not want Europeans to get vaccinated. I wonder who that may be, with access to some offensive cyber units with free cycles? The leak contains very hermetic (biotech/pharma) language - impossible to decipher by laypeople. It also contains many various numbers. Risk of drawing wrong conclusions. Some people enhancing their confidence in their chosen beliefs, sowing distrust in the process of vaccine registration, and vaccination in general.
But if this operation was supposedly for cyber espionage purposes, why would the attackers make the stolen data public? This is no longer about espionage.
SolarWinds hack. So, who is behind? Some say Russia is, and here are some others who point to the Turla group’s malware being found in use. Conclusions are unclear. One (among others!) of the potential options is fascinating: “developers introduced these subtle links as a form of a false flag”. Another analysis from the investigating team describing the toolset used to compromise the SolarWinds/Orion build system. This is how the malware eventually reached the victims. Other software vendors are likely at risk of being the target of similar operations.
When SUNSPOT finds the Orion solution file path in a running
MsBuild.exeprocess, it replaces a source code file in the solution directory, with a malicious variant to inject SUNBURST while Orion is being built.
Ships, ports, and so on. U.S. released a national plan for cybersecurity in the maritime sector.
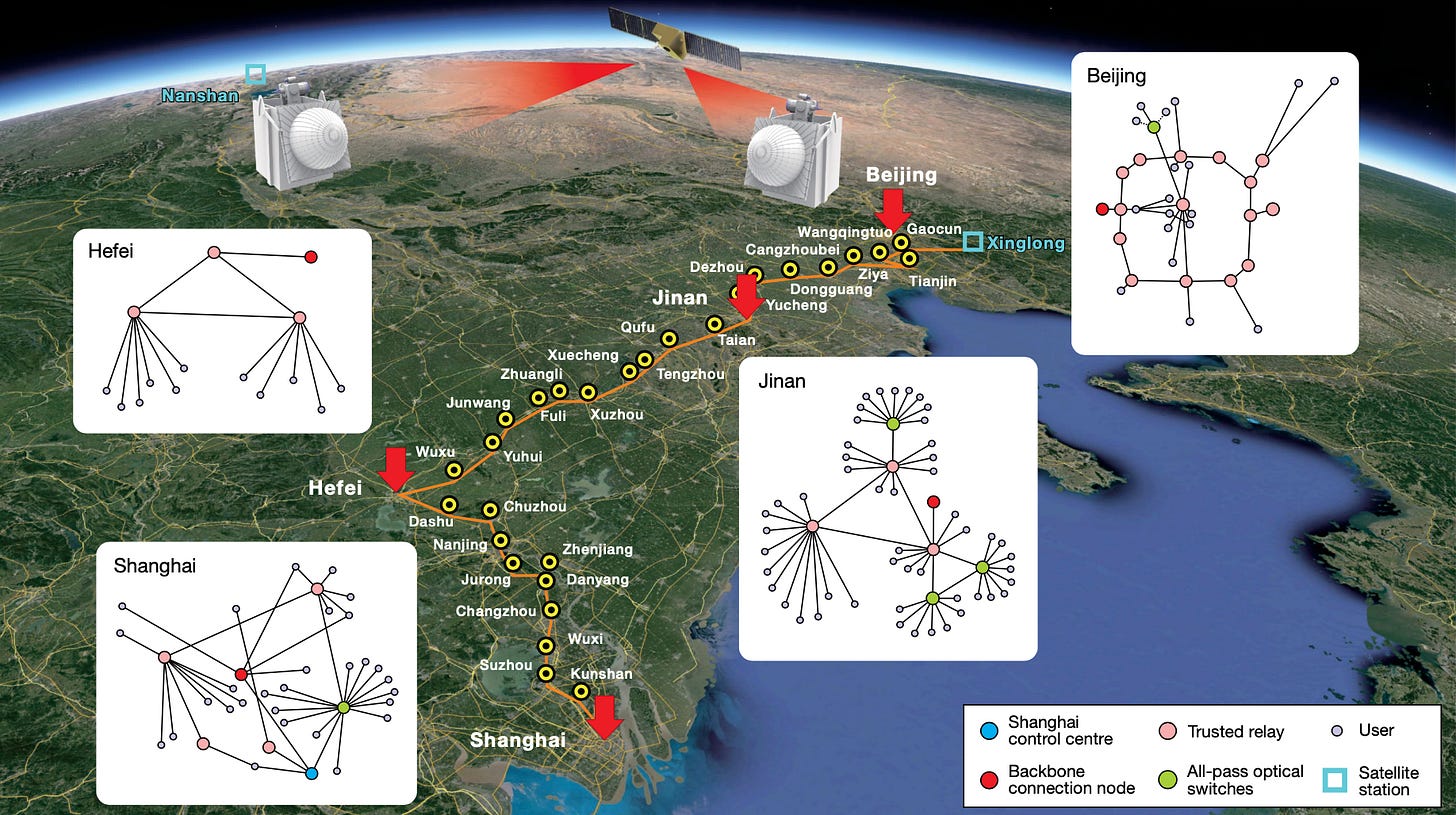
QKD link. It’s more about science. China demonstrated an impressive quantum key distribution (when done right, enables encryption with unconditional security).
by integrating the fibre and free-space QKD links, the QKD network is extended to a remote node more than 2,600 kilometres away, enabling any user in the network to communicate with any other, up to a total distance of 4,600 kilometres (…) quantum technology is sufficiently mature for practical applications. A global quantum network can be realized (…)
4,600km distance is significant because such demonstrations in practice still tend to be limited by distance. The issue is hardware and infrastructure. It’s fair to say that China is already the leader in this field. Impressive deployment.
Privacy
U.S. Federal Trade Commission ordered a company offering facial recognition technology to purge a trained machine learning model. Such models often contain private data. As such, this is processing personal data. There is evidence that it is possible to extract private data from machine learning models.
AI/ML training models may contain private (personal) data. As such they are sensitive. Case closed. To ‘train a machine learning model’ requires to process data - and it simply embeds what it “learns”. Examples including the inference "if given data record was part of the model’s training dataset or not" or "recovering secret features used in the model" are clearly attacks on artificial intelligence models with implications to privacy/data protection.
GDPR vs State use of drones. French DPA sanctions the French Ministry of Internal Affairs for the use of drones with cameras, for example, in use in the surveillance of demonstrations. The DPA CNIL ordered the ministry to stop. This is a GDPR breach but no fine. The DPA in France is unable to fine public institutions (immunity).
ServiceWorkers history sniffing. ServiceWorkers make the web faster and often offer performance and usability gains. Now it turns out that they can also be used to track web users, and even steal the list of user-visited websites. Here’s an explanation of surveys indicating that web browsing histories are private/personal data.
Technology Policy
Bans, suspensions, filterings. Twitter suspended around 70k accounts in some way linked to the previous week’s violent events in the U.S. “accounts that have Tweeted or Retweeted associated content will continue to be subject to limited visibility”. Some politicians express a feeling of being cut out from their electorate with such preferences.
Disinformation/PR for hire. Report finds 48 countries employing professional disinformation (PR activities) services to engage in campaigns attacking the opposition, trolling, and so on. The report does not weigh to what extent such activities subscribe to the quality and level of the domestic situations, and it focuses on the actions of the governments (perhaps also the ruling parties?). The report is based on an analysis of public press articles (and some other secondary content).
China’s approach to technology development. “China’s quasi whatever-it-takes approach to public support for the semiconductor industry has led to severe waste and misallocation of resources. (…) This is a persistent weakness of China’s state capitalism. At the same time, the system allows waste, and waste in some projects does not mean that all projects will fail. Winners emerge in spite of waste, as public funding does not entirely evaporate.”
That’s it this time, thanks!
In case you decide to forward this letter further for any reason, I’ll leave this thingy below: