TechLetters #117 Cyberwar in Ukraine; SAS down; Responsible Military Use of Artificial Intelligence; extracting private data out of AI/GPT-like systems; western 'hacking group' hacking China
Security
US NIST is calling for new cryptographic submissions. Multi-party threshold schemes.
Mail bomb in US Army. Thirteen thousand members of the United States military caught in an email storm. So-called "reply to all" problem, in early February. You know this well, probably. Everyone got theirs. A sophisticated denial of service. "Some of the humorless officers resorted to typing "PLEASE REMOVE ME FROM THIS DISTRO,". That probably didn't help.
Network of Scandinavian airline SAS compromised, user data breached. Website went down, their app was working badly/wrong. "customers who tried to log into SAS app were logged onto the wrong accounts and had access to personal details of other people". Weird! “During Tuesday afternoon SAS was, among others, the target of a cyber-attack that affected the app and website”, the airline said on 14.02.23, but then the breach notification was removed from their website. In unrelated news, a cable-cut causes massive IT issues for the German Lufthansa airline. Many flights were cancelled. Unrelated to a non-event alleged “cyberattack” (DDoS) on German airports and it is nonsensical to find any links here.
Cyberwar in Ukraine. A report of cyberwarfare in Ukraine. Cyberwarfare, information warfare (and operations). The take-away assessments are quite obvious. Phases of cyber operations identified. What’s striking is that making such assessments was possible quite well by only basing on public-available information. The report also, first in such a way, highlights how Belarus is party to the armed conflict against Ukraine. Cyber/information warfare activity clearly linked "campaigns against political and defense-related targets, as well as NGOs and organizations assisting Ukrainian refugees". The report confirms that multiple countries are active in this cyber conflict. China is making cyber operations (espionage; not as a side to the armed conflict). That’s not all, but the rest are not covered in the report. Another fact also often omitted in Western analyses. Russian information operations are primarily aimed domestically. Still, this report does not cover an interesting information operation directed at Russian society with anti-war messages (that was a curious one, in first days of the war).
Responsible Military Use of Artificial Intelligence and Autonomy. Released by the USA. Critical topic due to the recent progress (ChatGPT, use of new tech in Ukraine war). "Use of AI in armed conflict must be in accord with international humanitarian law". How to comply legally and technically is another issue.
60 States call for responsible development/use of AI in military applications. The call. “failure to adopt AI in a timely manner may result in a military disadvantage, while premature adoption without sufficient research, testing and assurance may result in inadvertent harm”
Twitter will effectively disable a security feature. Two-factor authentication (2FA) will be disabled automatically. Unless you pay $8 a month. You may opt to other 2FA method. Probably most users won’t. They’ll get degraded security. Automatically!
Chinese analysts identified ‘Western’ cyberattack group. Hacking targets in China.
Privacy
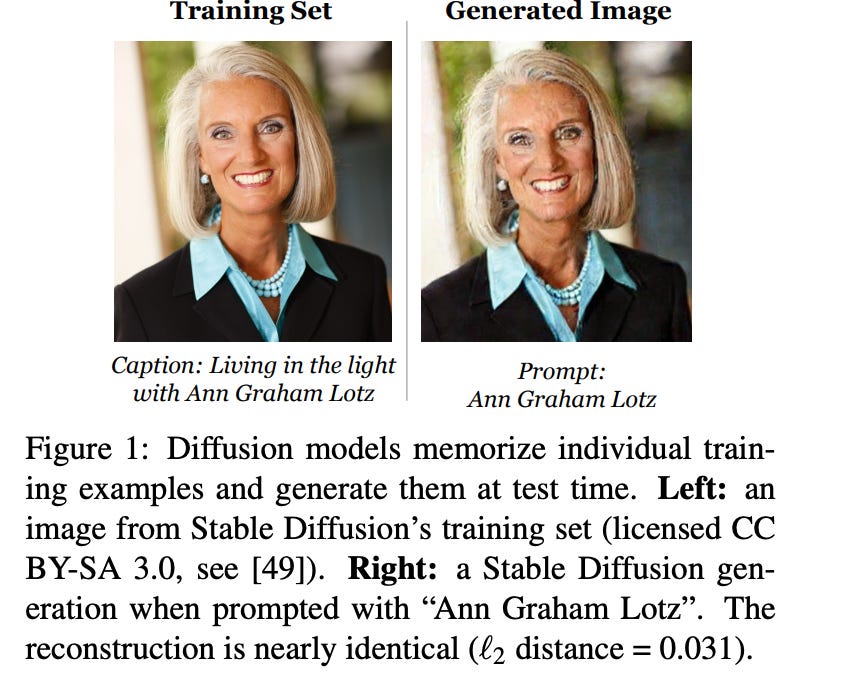
It's possible to extract data from the training 'models' of 'AI' systems Like DALL-E, 'stable diffusion', etc. Implications for privacy, ethics, copyright. Very inconvenient evidence. Misuse of copyright and a massive privacy breach? One wonders about the future regulatory liability.
Other
A HUMAN defeated ARTIFICIAL INTELLIGENCE in the game 'Go'. It was "surprisingly easy". Just had to find a weakness, a flaw, a vulnerability in the AI system and then exploit it. Therefore it was adversarial. Fundamental weakness of AI systems.
In case you feel it's worth it to forward this content further:
If you’d like to share: