TechLetters #14 - cybersecurity vulnerabilities in weapons systems, hacking belligerents during an armed conflict, cyberattacks on water treatment facilities, hacking to fund nuclear weapons programs
and a global tracking ID for all internet users
Welcome to the 14th letter
Éditorial
When you’re a policymaker and you don’t like a particular feature of modern life, what do you do? Criticise it. Express concern. Possibly include the critique in many places. This would let you to refer back to it as a matter of fact, arguing that “this fact is reflected here and there”.
This is maybe what is happening in Europe with end to end encryption (E2EE), the current gold standard of communication confidentiality. We know of critical voices around the world. Many policymakers express them. In Europe this recently went much further:
Recent cybersecurity regulation proposal is suggesting that encryption features should be reversible (so no E2EE)
Recent privacy regulation is suggesting that encryption features should be reversible (so no E2EE)
Where this leads is anyone’s guess.
But some may perhaps stop pretending that nothing is happening. Such changes do matter.
Security
Military cyber. More information about the UK’s military cyber operations targeting ISIS fighters. Hacking drones and generally creating an expectation of unreliability in the victim. It's like to “turn the use of online operations as an ISIS vulnerability”. Yes, that’s one way how military cyber operations can work. Previously, some other details were previously revealed by Australian services. Was this campaign a cyber military test-bed?
Cyber chemical tampering. Someone broke to the control systems of a US city of Oldsmar and changed (attempted to) the chemical composition of water in a treatment facility… That could have poisoned thousands of people. The potential humanitarian catastrophe was averted. The attackers "likely accessed the system by exploiting cybersecurity weaknesses, including poor password security, and an outdated operating system. Early information indicates it is possible that a desktop sharing software, such as TeamViewer, may have been used". It’s advised to install physical precautions:
Examples of cyber-physical safety system controls include: o Sizeofthechemicalpump
Size of the chemical reservoir
Gearingonvalves
Pressureswitches,etc.
The benefit of these types of controls in the water sector is that smaller systems, with limited cybersecurity capability, can assess their system from a worst-case scenario. The operators can take physical steps to limit the damage. If, for example, cyber actors gain control of a sodium hydroxide pump, they will be unable to raise the pH to dangerous levels.
Another NotPetya litigation, dismissed. U.S. Court dismisses a suit related to NotPetya cyberattack/wiper campaign in 2017 ("withholding" information about the extent of damage). This is one NotPetya litigation you've probably not heard about (there are more, related to insurance). How companies communicate about the consequences of breaches is very important. It must be transparent enough but at the same time cautious. Here are the initial court documents.
Cyber funds nukes. United Nations report indicates that North Korea is funding their nuclear weapons development program with funds stolen via cyberattacks.
Hacking customers of a particular vendor via a custom product-level implant. Bloomberg is repeating the claims that SuperMicro was infecting customers with tampered hardware, enabling hacking of their networks. This will be. controversial but details are "confidential", so little point in arguing about "evidence". Trust, or not.
Overall, the findings pointed to infiltration of Supermicro’s BIOS engineering by China’s intelligence agencies, the six officials said. … Small batches of motherboards with the added chips were detected over time, and many Supermicro products didn’t include them, two of the officials said.
Cybersecurity Requirements for Weapons Systems. Like the lede says. Here. “A weapon system is a combination of one or more weapons with related equipment, materials, services, and personnel, and with means of delivery and deployment. The threats to weapon systems include equipment failure, environmental disruptions, human or machine errors, and purposeful attacks, such as cyber attacks”. “For example, the B-2 Spirit Bomber, one of the weapon systems we assessed, has been in the O&S phase for over 16 years. Due to the system’s age, it is continuously exposed to changing threat environments and new cybersecurity vulnerabilities’”. Good luck with securing a 16-years-old system. Also, I can imagine how ‘fun’ it is to audit the cybersecurity of a B-2 bomber. Or, say, a missile. Now Imagine - why not - a missile defence system hijacked by hostile belligerents. Also, such tests redefine the definition of “what can go wrong”, or also “testing on production”.
Privacy
ePrivacy, what? Council of the European Union delivered their version of the much contested file. I offer an analysis, with critique and suggestions of changes. I must say that I’m particularly surprised that this regulation that was about confidentiality in electronic communication could potentially undermine end to end encryption systems.
Global tracking ID. Australian competition authority is conducting an investigation into transparency/etc in online advertising.
Proposal 6 – Implementation of a common user ID to allow tracking of attribution activity in a way which protects consumers’ privacy
Introduction of a secure common user ID, which ad tech providers would be required to assign to any data used for attribution purposes. This should be done in a way that protects the privacy of consumers.
Introduce a global user ID to improve competition in online ads? It would be hard to reconcile it with privacy, that this proposal would go directly against.
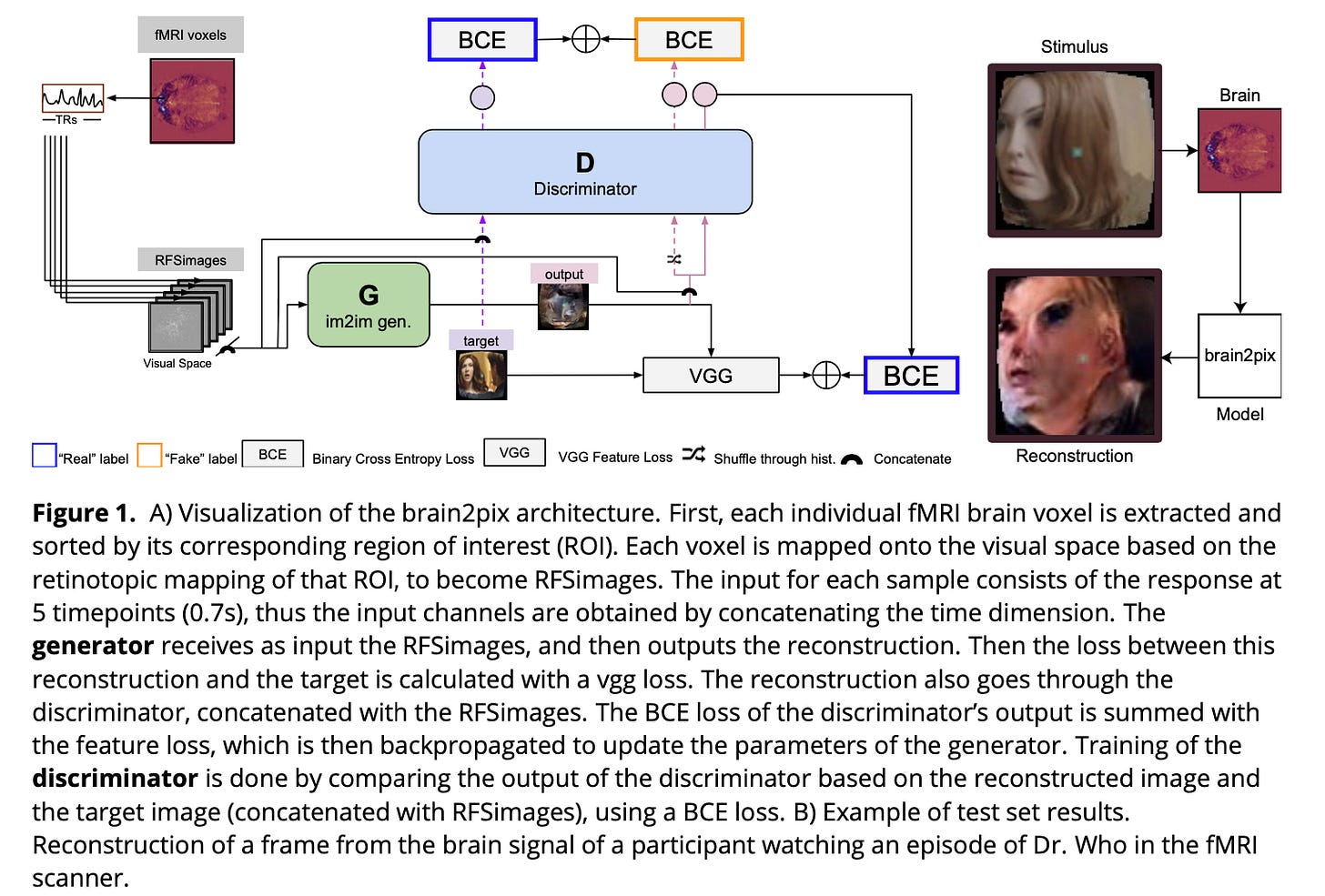
Brain waves to video. Interesting machine learning paper describing how to “convert” brain wave measurement into a video… Brain activity is scanned with a fMRI.
Technology Policy
European chips. European Union wants to boost tech sovereignty with building a local chip foundry. For many reasons this makes sense. Maintaining the previous-20-years approach of outsourcing everything is increasingly not sustainable. “Once a hub of semiconductor factories, Europe has dramatically cut back on manufacturing over the past 20 years, … preferring to outsource a major chunk of production to giants like TSMC’”
That’s it this time, thanks!
In case you feel it's worth it to forward this letter further, I leave this thingy below: