TechLetters #23 - Deepfakes OK? Vulnerable IoTs. SolarWind hacks in Europe. Cyber sanctions, Russia twice. Hacked cheese.
Editorial
European Unions plan on AI leaked. It emerged that the use of deepfake technology will be allowed, sometimes with "appropriate disclaimers”, at other times without. Anyhow, this sounds like a potentially transformative change possibly with an impact on whole societies, including political systems.
The problem is, people are kind of bad at spotting such fakes. Imagine the use in elections, for example. Can (and should) this be done legitimately?
Interesting times, aren’t they.
Security
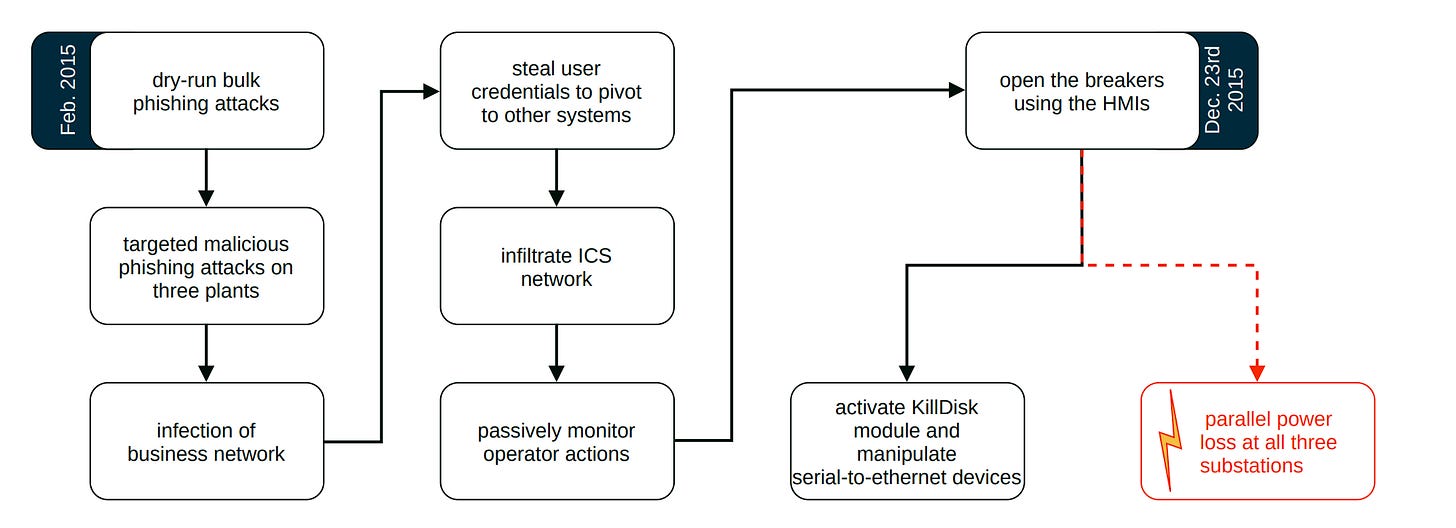
ICS malware. Nicely described industrial control systems malware used in actual attacks that caused power cuts or may have caused physical damage.
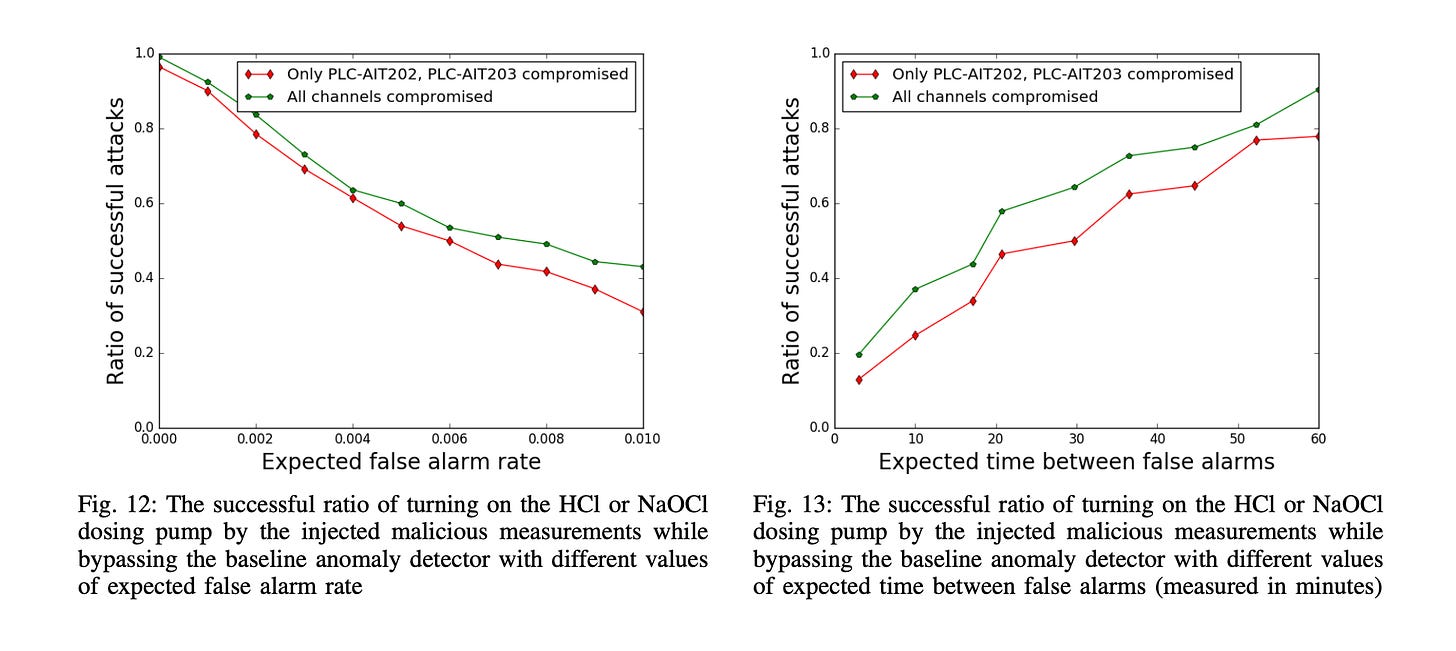
Deepfake-tech-like attacks on industrial sites. “A Deep Learning-based Framework for Conducting Stealthy Attacks in Industrial Control Systems”. “by intercepting the sensor and/or control signals in an ICS for a period of time, a malicious program is able to automatically learn to generate high-quality stealthy attacks which can achieve specific attack goals whilst bypassing a black box anomaly detector.”
100M of IoT vulnerable. “if we conservatively assume that 1% of the more than 10 billion deployments are vulnerable, we can estimate that at least 100 million devices are impacted by NAME:WRECK. The new vulnerabilities allow for either Denial of Service or Remote Code Execution” (link)
Financial cyber risk. “One nightmare scenario, Powell said, would be if hackers managed to shut down a major payment processor — hamstringing the flow of money from one financial institution to another. That could shut down sectors or even broad swaths of the financial system”
Cyber cheese breach. Ransomware infection at a Dutch logistics&transportation company led to cheese shortage. "disruption led to a shortage of certain food products, especially cheese".
SolarWinds hacks in Europe. 14 Institutions, Bodies or Agencies of European Union used SolarWinds/Orion. Six of them are confirmed affected. Apparently, password resets happened in the systems used by the European Parliament.
Cl0p? "cybercriminals are trying to recruit customers of the breached companies to help them exhort the companies they hacked". In addition to encrypting the target’s data, stealing the data, and leaking the data (link).
License to Hack. U.S. Justice authorised the FBI to hack into hundreds of american companies. To remove malware.
US sanctions Russian entities. For cyberattacks, including SolarWinds operation. This story is quite rich. Sanctions are tough: prohibition “from participating in the primary market for ruble or non-ruble denominated bonds”, some people added on sanctioned entity lists, and called-out companies. In one case, one cybersecurity company (Positive Technologies) added to the list is being reported by the media as someone who actually ran cyber operations for the state, or for their own reasons (Links: 1, 2). The move is supported by the UK who repeats the formal attribution of the cyber operations, and NATO, and European Union. What to expect now? Russian Federation saying that it’s not them. But the companies brought on the sanctions list will not escape so easily.
Supply-chain hack. Compromise of Codecove development tool. "beginning January 31, 2021, there were periodic, unauthorized alterations of our Bash Uploader script by a third party". Thousands of projects affected?
Privacy
Contact-tracing blocked. An update to UK's contact tracing application was blocked by Apple/Google. The update desired to expand the scope of processed data to include also location data. This is prohibited by the policy of Google/Apple contact tracing framework.
Technology Policy
Russia’s new principles for technology policy. “Fundamentals of State Policy of the Russian Federation”. “Russian Federation intends to promote "the creation at the global, regional, multilateral and bilateral levels of an effective mechanism of interstate interaction aimed at preventing computer attacks on information resources of states, including critical information infrastructure” says the document. My short&quick look here. Idea to set up a cyber-incident-settling agency?
Other
Bitcoin energy use. “Policy assessments for the carbon emission flows and sustainability of Bitcoin blockchain operation in China” (link)
In case you feel it's worth it to forward this letter further, I leave this thingy below: