TechLetters #51: Cyberattacks disrupting healthcare. Tricking code reviewers. Active cyber defence? China’s new data protection law
Éditorial
Impressive long-term strategic planning! Obviously technology & geopolitical environment today is totally different than 200 years ago. It was impossible to predict this. Yes, long-term planning has risks. But some projects still require long-term approach. For example: climate change policy, next-gen fighter jet project, space technologies, etc. And Danes? They at least have a nice oak forest.


Security
Cyberattack disrupted healthcare provisioning in Canada. Situation is serious enough to warrant a Minister to speak up. Ransomware in healthcare is always a threat to human life (“largely working with paper-based backups”).
Allegations of Indian of cyberattacks on Chinese government, defence and military units.
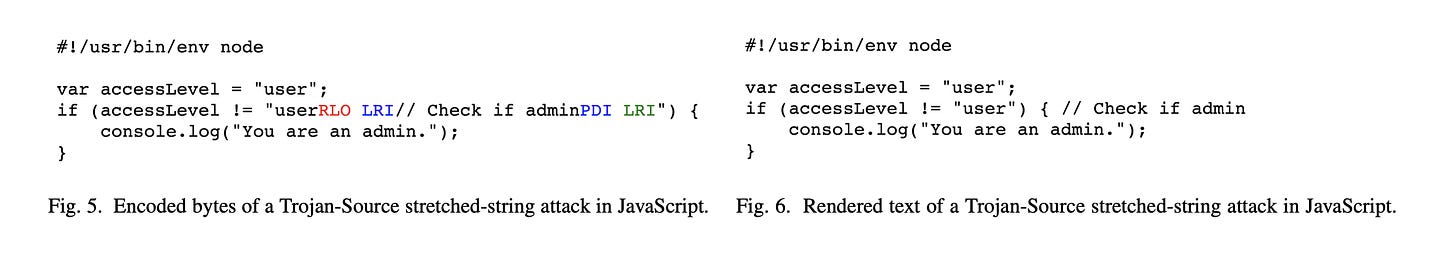
Tricking code reviewers. To introduce backdoors. "New type of attack in which source code is maliciously encoded so that it appears different to a compiler and to the human eye. This attack exploits subtleties in text-encoding standards such as Unicode"
US military on China. “Cyberspace operations as a means of achieving information dominance early in a crisis or conflict" (pdf)
Active cyber defence. SNV think-tank report on active cyber defence operations. I was in the expert group working on this report. “The objective for any active cyber defense operation is to technically neutralize and/or mitigate the impact of a malicious cyber operation or campaign and/or attribute it technically. The technical attribution can then lead to the implementation of addi- tional response (political) mechanisms such as sanctions”
Cash for information. U.S. State Department is offering $10 million for information leading to the identification or location of leaders of the "DarkSide ransomware variant transnational organized crime group", $5 million for information leading to the arrest of coconspirators. These groups are responsible for Colonial Pipeline disruption.
Privacy
China’s new data protection law. China’s Personal Information Protection Law in force. New trend in China: demand for data protection officers. I suspect that, exactly as in the EU (with GDPR), most of the people/candidates will not actually be up to the task. Still a problem in EU.
ePrivacy lobbying. ePrivacy Regulation is currently maladapted with GDPR. The process is stalled. Some Big tech (GAFAM) corps actively worked to get such an outcome. Olympic Games of lobbying? The current framework for protecting privacy in electronic communication is obsolete. The negotiated new #ePrivacy Regulation is almost obsolete by now, too. Read about the work process here.
Purging face recognition at FB. Facebook/Meta will shutdown their face recognition system, remove billion+ of photos. This is a great and a positive move. We have no reason not to trust them. This is a positive move privacy-wise and human rights wise. However, one caveat: they will NOT remove the actual face recognition system (DeepFace), which was created likely based on the trained data (that are apparently no longer needed?). The point is that such a learned model basically “contains” the images (they are “learned”), and constitutes personal data, too. There are many examples of inference attacks on machine learning models, or even data extractions. The actual process of phasing out could be a perfect case study of phasing out a product processing personal data on a grand and visible scale! This is rarely seen in public. #GDPR has a detailed process for that. It must be considered on the level of the data protection impact assessment.
Technology Policy
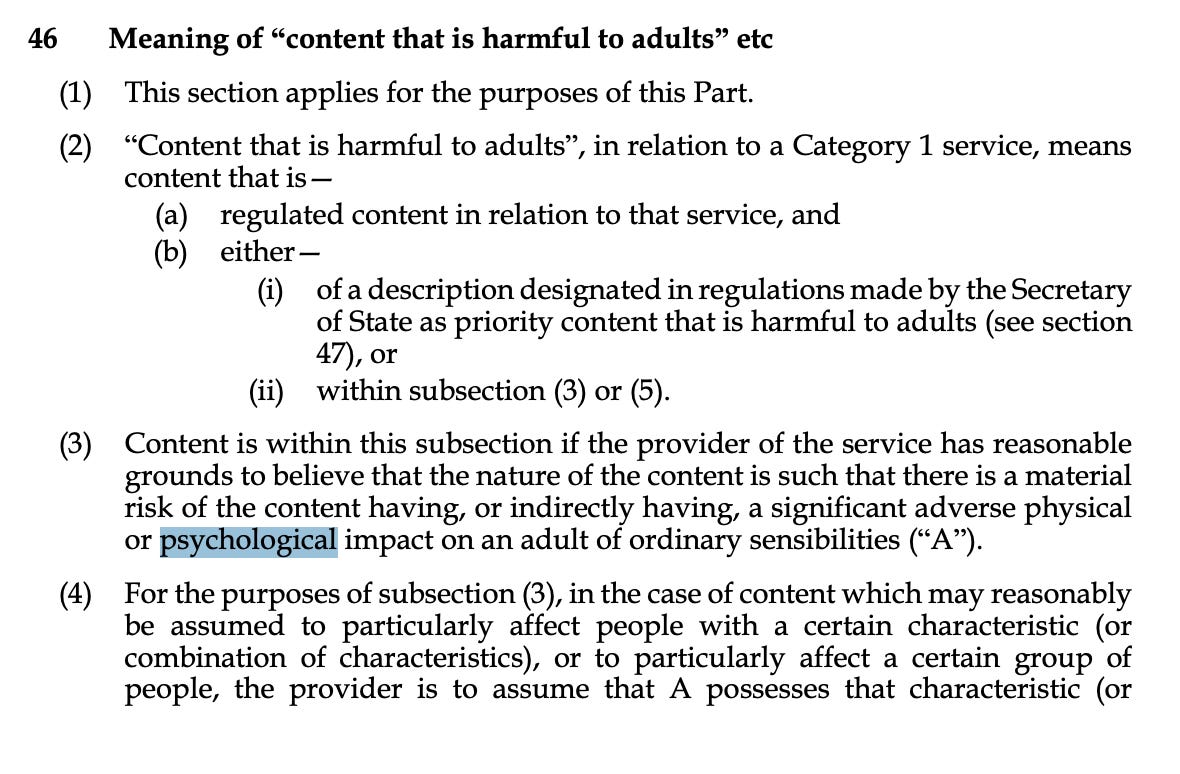
Online Harms Bill. UK to implement content moderation/censorship rules on online platforms. Content that may have a "harmful psychological impact" - prohibited. Interesting consequences for advertising, political PR, etc - which, by definition, have psychological impacts.
Other
In case you feel it's worth it to forward this letter further, I leave this thingy below:
You may also share here: