TechLetters #75 - Ukraine cyberwarfare in 2022 has roots in 2021. Russian cyber operations, Chinese cyber operations. Worms and ransomware for industrial control systems. US cyber weapons?
My input about transparency of cyber tools.
Also, very likely there’s no newsletter next week. We’ll see.
Security
US is offering $10 million for information on GRU cyber operators involved in NotPetya cyberattacks. Disclosure here. If you feel like it, you can report it here.
Cyberattacks on industrial control systems. Self-propagating worm for industrial control systems. "Infected PLCs may be distributed by a supplier of an industrial component or during the transport of such a component". It can be armed. Ransomware for industrials control systems, demanding payment to un-disrupt systems, with optional functionalities to damage industrial process, or even effect in health damage or death of personnel...
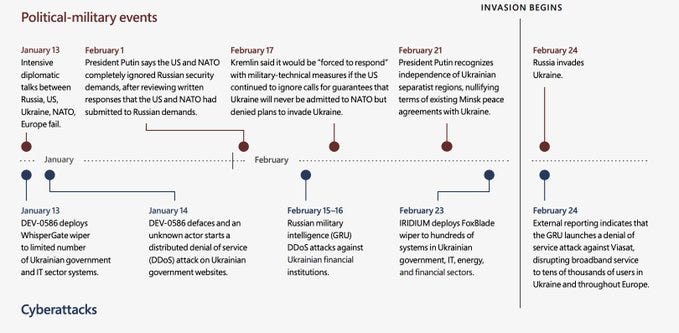
Cyberwarfare on Ukraine — some activity started in March 2021. Range of Russian cyber operations in Ukraine, including those targeting critical infrastructure. 6 actors active just prior to the land invasion. Espionage and destruction. Correlated with kinetic warfare operations. Preparations for some of those war-time cyber operations started as early as in March (!) 2021. Some cyber operations looks to be aligned with non-cyber military operations (or at least can be linked this way).
Potential Russian aim of cyberwarfare operations on Ukraine."extensive details on much of Ukraine’s population". Potentially useful to identify/locate Ukrainians likely to resist, "and potentially target them for internment or worse". Tangible gains of cyber operations, after the analysis, the information could later be passed over to the forces operating locally (land-based). You cannot exclude that.
US Special Ops Command to fund new science-tech efforts in cybersecurity. Development of new operations capabilities. Including development of destructive cyber payloads, engaging SCADAs (industrial systems), bypassing air-gaps... "next generation effects"
China's cyber intelligence group activities re-tasked. It now "appears to be changing its targeting in response to the political situation in Europe and the war in Ukraine", targeting "Russian-speaking users and European entities". New tasks arrived!
Seems that smartphone inspections of Ukrainians fleeing cities via Russian 'filtration camps' are routine. Like explained here. Best approach is to have all potentially risky data wiped, but not everything because this would look suspicious, too (and looking suspicious is not a good idea). It is also impossible to argue about a forgotten PIN. Sorry, that's how it works, and tech is not exactly of help here when you argue with armed personnel.
Privacy
Technology Policy
Upload filters are legal. European Court of Justice ruled that the copyright directive’s article 17 is legal. So “upload filters” that would inspect the content that the user wishes to upload - are legal, and according to the ruling, the necessary “safeguards” exist. Still: “In order to carry out such a review, the providers must use automatic recognition and filtering tools. Such a prior review and prior filtering are liable to restrict an important means of disseminating online content and thus to constitute a limitation on the right to freedom of expression”.
US+60 countries announced Declaration for the Future of Internet. "Protect human rights and fundamental freedoms of all people", " avoid Internet fragmentation", security, privacy, and more. Here.
Other
Internet access malfunction in several cities in France. Shutdown or slowdown effects. It is quite mysterious, coordinated action across the country. Physically cutting cables (optical fibers). Notable: those places are not actually easily accessed. Sabotage touching connectivity in Lyon, Grenoble, Paris, and more.
The future of artificial intelligence (AI) in workplace applications. Puzzling at least. Calculation of "Employee Score", and employee monitoring/tracking: "The score is made up from many components, but it includes what an AI sees when it examines the text of a worker’s emails and chats to purportedly determine their sentiment, or changes in it, that can point towards disgruntlement. The company can then subject those people to closer examination. ..." ...
In case you feel it's worth it to forward this content further:
If you’d like to share: