TechLetters Cyber Insights: Cyberoperation as a prelude to Ukraine 2022+ war, a year after
Cyberoperations gradually escalated the situation, and were a signal. Especially one.
This insight and assessment is about cyber operations and may hold value for cyber threat intelligence.
The land invasion of Ukraine by the Russian military on 24.02.2022 was a major escalation. The event was preceded by a wave of cyberattacks, their culmination in January and February.
An initial message must precede the rest of the analysis. It is important to appreciate that too many Western/EU policymakers/pundits/analysts overreacted in January, risking the inability to see things in the right proportions and therefore potentially forfeiting ways of proportional activities once things got even more serious. That said, the current humanitarian in military aid is just the right reaction one should expect; still — such a scale of measures wasn’t (at least in public) considered in early 2022. As this is a different topic - I will not continue it. This post is about a single cyber-enabled information operation, impact assessment, and the potential insight we may have in the future.
You probably read a lot about the employment of various wipers, and perhaps the crippling of a satellite communication system, too. Anyway, where’s this prelude to war? If we were to consider the potential link, or path, from the initial diplomatic coercion, that would take advantage of a cyber operation, we must look at the single event taking place exactly one year ago, on 13.01.2022 when a lot of Ukrainian government were breached and defaced.
Cyber-enabled information operation
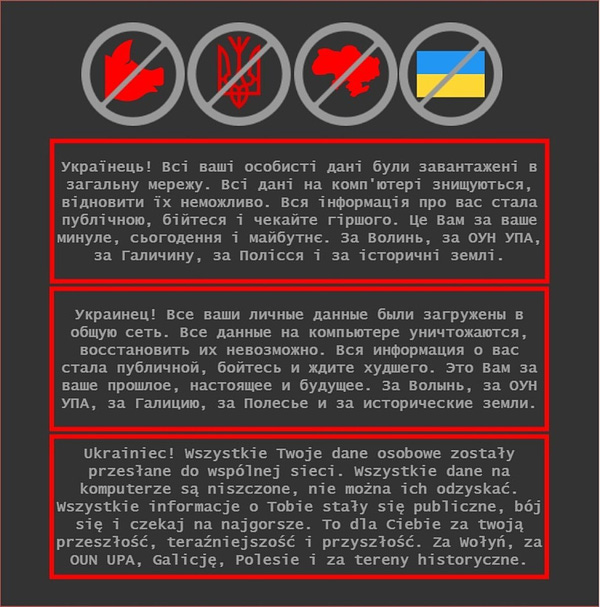
Those pages had this message posted (in Russian, Belarusian, and Polish) on them:


It was a cyber-enabled information operation. The cyber operation element involved the use of a supply chain vulnerability to access the content management system (October CMS, using this vulnerability) to post to the site. I quote it here in English (the aforementioned grammar mistakes do not translate very well):
“Ukrainian! All your personal data has been uploaded to a shared network. All data on the computer are being destroyed, it cannot be recovered. All information about you has become public, be afraid and wait for the worst. This is for you for your past, present and future. For Volhynia, for OUN UPA, Galicia, Polesie and for historical areas”. It is immediately clear that the original input text was composed in language that does not have a grammatical vocative case structure, for example Russian language.
It’s a screaming fake, that is quite clear
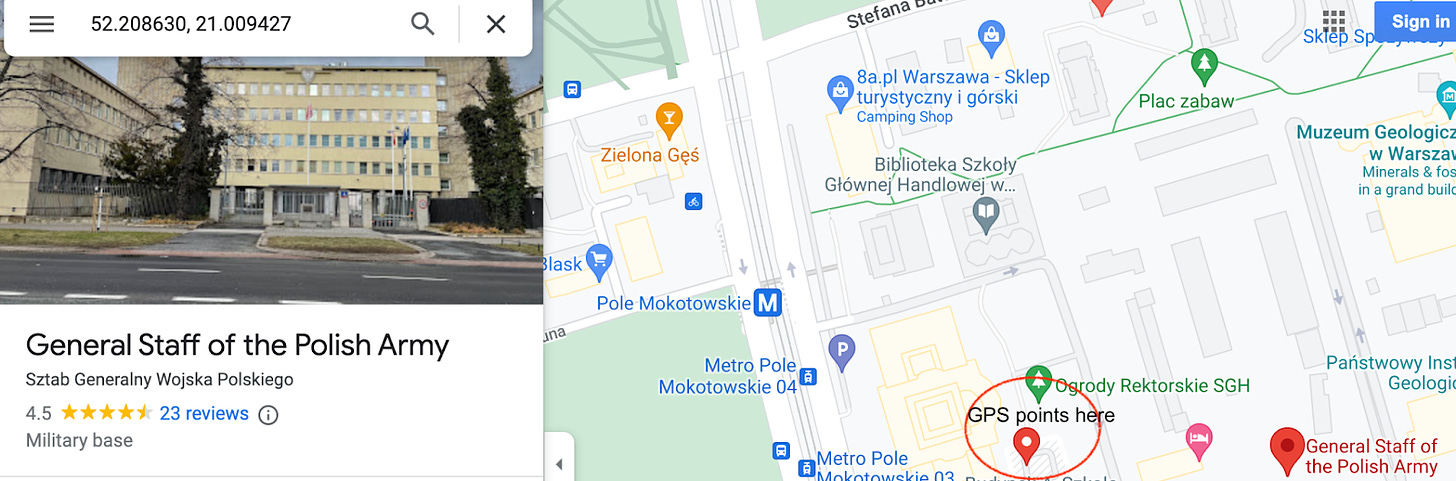
The author of this message posted to the hacked Ukraine government sites used machine translation so that obvious errors are evident in the Polish translation (I’m not performing a full lexical analysis here; there’s no need for this). The images were also tampered with to contain artificially added metadata potentially pointing to the location (GPS: 52.208630, 21.009427) of the main headquarters of the Polish Armed Forces in Warsaw/Poland. There is no way such metadata are included during normal image creation (as it was not a photo), so it’s either a botched attempt to plant a false trail, or some kind of a message. We don’t know.
Interestingly, some big media outlets like the Financial Times apparently had a hard time correctly weighing, analysing, and perceiving the event.

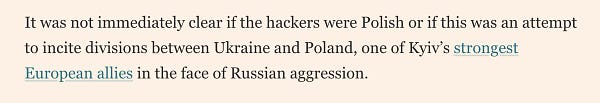

While I understand the media's needs, and rationale, for example giving voice to many sides. However, giving credence, and a wide audience, to potential perpetrators from a military intelligence of a country planning a major military aggression still sounds quite eccentric. Though I’m not a journalist, so perhaps I am not the ultimate authority here, so you be the judge.
Still, unambiguously, the posted message played on some historical resentments between Poland and Ukraine. Hard, and difficult historical facts and events. That said, considering that Poland is a de facto help hub to Ukraine via which Western help transits, the gravity of the issue - attempted implantation of the resentment messages early on, amplifying it - is clear.
I brought attention to this on several occasions. Miraculously, and also very fortunately, the above-mentioned article is now pruned from that content (though no trace remains explaining the edit). That is very fortunate, and I commend Financial Times for this change.


The need for caution
However, in the future, social media accounts with big follower count, or the media, should be wary of being instrumentalised in attempted information operations. In this case, perhaps even the use of (too often abused; don’t do that, too) the term “information warfare” is completely justified. Fortunately also some other outlets were more cautious in reporting this particular event, like the French Le Monde.
Assessment
The subsequent land invasion was obviously not “caused” by the cyberattack.
This cyberattack was also not its initiation, for sure.
But if we were to point to a single cyber-related event that is most clearly linked with the later land invasion and aggression, it would be it.
Impact rank
What’s the severity of this event when seeing it as a single intervention? I invite you to use the analysis metric explained in the previous Cyber Insight, the cyber escalation ladder and impact-driven assessment , if only because it is objective and based on the decades-old framework that still sticks.
Using the cyber impact level of this model, the event described in this post unambiguously, at a minimum, deserves a grade 1 (sovereignty violation), and perhaps grade 2 (interference in domestic affairs), at the maximum. It does not exceed it. It is, clearly not for example, the use of force. This constrains any sensible or reasonable responses or retaliations to a single event of this kind. But as we’ve seen, later on, an entire land invasion and aggression occurred. And this single event can likely now be linked to it.
Interpretation of cyber-events is tricky
The interpretation of this event should highlight that cyberattacks/cyberoperations are an integral part of statecraft, both of offense, defense, or signaling intentions/escalations. It is also tricky to weigh events of this kind and measure their seriousness. While the above event evidently could be seen as a serious and worrying event (especially when put in context of other events), I would, for example, not classify some other activities with similar seriousness, for many reasons.
The overall event highlighted the shortcomings in preparation of many Western/EU policymakers, possibly including their analysts or assistants. It seems to me that in many cases, the replies, when/if expressed, missed the point. What’s worse: the single event above was largely missed, in itself, and the focus was “more general”, on other aspects “in general”, like “whatever cyberattacks”. How to cope with that is not in my remit. Chances are that we’ll gradually gain competencies in this relatively new field, so the issue will, maybe, eventually solve itself. Let’s just hope that “in the meantime” it won’t cause any inadvertent problems.
There will be much more about this topic in my book, currently, I am finalising the manuscript for the Publisher.
Did you like the assessment and analysis? Any questions, comments, complaints, or offers of engagement ? Feel free to reach out: me@lukaszolejnik.com