TechLetters ☕️ Filling social media with bots. China's cyber operations vs U.S. with unclear goals. Trump administration vows to retaliate. Cutting subsea communication cables because it's 2025
🎇 Happy New Year Summary🎆 https://blog.lukaszolejnik.com/summary-of-2024/
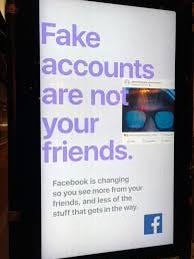
Is Meta envisioning filling social networks with AI-generated bots that would blend with humans?
Making it in ways indistinguishable from humans would be illegal considering EU AI Act. My assessment. https://blog.lukaszolejnik.com/filling-social-media-with-indistinguishable-ai-bots-is-illegal-with-eu-ai-act/
How times change. The following ad campaign was ran by Facebook itself not that long ago.
Security
The U.S. Treasury was hacked allegedly by China. With its workstations compromised and data stolen. A contractor of identity access company BeyondTrust was also compromised when attackers "gained access to a key used by the vendor." This raises serious security concerns.
Chinese cyber operators gained control to shut down U.S. ports, power grids, and other critical infrastructure. Intrusions were severe, with key details lost due to erased logs and inadequate tracking. China’s military infiltrated infrastructure such as a water utility in Hawaii, a Houston port, and an oil facility, maintaining control for years and periodically testing their access. The cyber operators (sometimes called “hackers”) exploited unpatched Fortinet devices and Cisco routers. They gained control of a high-level account without multifactor authentication, accessing over 100,000 routers and weakly secured telecom data pathways. Targets on Guam and the West Coast suggested attempts to delay U.S. responses in a potential Taiwan invasion, while other targets like air-traffic control and water-treatment facilities pointed to efforts to disrupt civilian life. Cyber operators breached phones of senior U.S. officials, accessing audio from Trump, JD Vance, and campaign staff. Officials increasingly relied on Signal to avoid vulnerabilities. Cyber operators infiltrated wiretap systems at Verizon and AT&T, staying undetected for up to 18 months to assess U.S. awareness of Chinese espionage. The attacks highlighted vulnerabilities in infrastructure and communications, with delayed patching and lack of safeguards like multifactor authentication exposing systemic weaknesses. The Chinese embassy rejected the allegations, accusing the U.S. of spreading disinformation about cybersecurity threats.
Trump’s administration plans to get tougher on foreign cyberattacks. Vowing to “impose costs” on both private and nation-state actors. “For too long our country has been on defense when it comes to cyberattacks,” said Trump’s transition spokeswoman. However, while this approach sounds appealing, the U.S. hasn’t solely been on defense, and previous attempts to impose "costs" have already been made. Additionally, the complexities of espionage—often lawful in international relations—make this a nuanced issue. So what else can be done? Missile launch responses? No.
Other
LLMs for code generation. And how it works.
Chinese vessel Shunxing39 suspected of cutting a cable near the port of Keelung in Taiwan. This raises concerns about the security of telecommunications infrastructure, which relies solely on trust. Previously, "accidental" issues in the Baltic Sea. The affected infrastructure (cut cable) is the Taiwan-Japan-USA cable. However, despite what the commentary says, this is NOT a 'grey zone' operation. Since it happens below the threshold of war, it is a 100% peacetime activity.
In case you feel it's worth it to forward this content further:
Subscribed
If you’d like to share: