TechLetters Insights ☕️ Physical attacks on crypto holders - wrench assaults rising?
If someone keeps valuable crypto at home and controls it themselves, anyone who gets the key or recovery phrase can move the money quickly. Without a bank in the middle. That is why such attacks can rely on threats or violence instead of hacking. The attacker does not need to break the system, only force the victim to make a transfer.
France is an example here. Between 2024 and 2026, there were many violent incidents targeting people connected to cryptocurrencies or their relatives, usually in the context of ransom demands or forced transfers, and sometimes involving severe violence. There was also a separate thread about the potential use of access to state databases to identify and locate such targets.
Why cryptocurrencies?
Why may criminals chose going after crypto holders instead of other wealthy people? The difference is how crypto works.
If the user keeps crypto in self-custody, it can be functionally like keeping cash at home (in a mattress, a sock...). It sits in a wallet that only the user controls. Anyone who gets the key or recovery phrase (seed) can move the funds. Cash has to be physically stolen, but crypto can be sent in minutes to an address that is not immediately tied to a real name. Once the transfer is confirmed, it usually cannot be reversed.
A bank can stop a suspicious transfer, delay it, and in some scenarios reverse it (e.g., under procedures and legal actions). Recovering funds usually requires freezes, cooperation from banks, and legal actions. In banking, high amounts often trigger anti-money-laundering (AML) procedures and limits, and criminals would have to use straw accounts tied to an identity. In many cryptocurrencies there is no “central authority” that can, on request, stop a transfer after it has been sent to the network.
Under self-custody, the user is on their own. A password to an exchange account or a wallet’s recovery phrase (seed phrase) can unlock the funds. If most assets sit behind a single key, that can mean access to everything, with no bank in the middle and no “cancel” button.
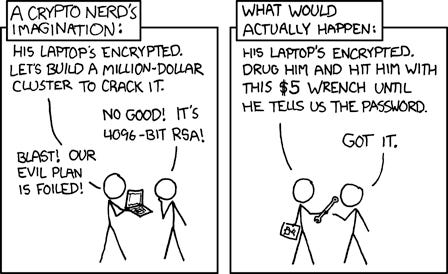
This enables the classic “wrench attack” scheme (an attack with a wrench), where violence replaces a technical attack.
The name comes from an internet joke: “Instead of breaking encryption, it is easier to use violence to force the password”.
Some people in the crypto scene publicly display their wealth and lifestyle, as can be seen in practices of showing off wealth on social media and at industry conferences. This makes target selection easier. Blockchain data can also show how much a given address holds. Identifying the person behind an address becomes easier once that address can be linked to a real identity.
By the way, in the EU there will be more systems with data on holders of crypto-assets. The DAC8 regulation introduces reporting on crypto-assets for tax administration purposes. Directive (EU) 2024/1640 also provides mechanisms that make it possible to identify holders of, among other things, crypto-asset accounts. This adds more datasets about crypto-asset account holders, held by public authorities and reporting entities, sometimes including account values.(including their value) on the side of the administration and reporting entities. (that saitd, it is all but natural that governments want to keep track of fund flows)
Data leaks from crypto firms may provide address and contact data that can be combined with information that a given person bought crypto hardware or services. After the Ledger leak in 2020, hundreds of thousands of records containing addresses and customers’ phone numbers appeared online. In early 2026 another data leak was described.
There are many more examples of such incidents. They are reported regularly.
What happened
Coverage in July 2025 described an investigation into a tax administration employee suspected of passing information to criminals. She allegedly looked up specific people in tax office tools and is suspected of sharing their data. Some leads pointed to targets connected with cryptocurrencies, alongside unrelated checks on other people, including recent burglary victims.
In November 2024, attackers broke into the apartment of an entrepreneur linked in press accounts to cryptocurrencies and held the victim inside. In a separate case tied to a ransom demand, June 2025 coverage described arrests linked to the abduction of an entrepreneur’s father, later found about 700 km away. In January 2025, Ledger co-founder David Balland and his partner were kidnapped. Not long after, another incident was described near Troyes, where a 30-year-old presented as a cryptocurrency specialist was kidnapped and later freed.
In early May 2025, perpetrators kidnapped the father of a person described as wealthy thanks to cryptocurrencies, and he was freed after a police assault. A few days later in Paris, coverage described an attempted kidnapping in broad daylight linked to the family of the head of Paymium.
Further cases in 2025 involved less publicly known victims but followed the same logic of coercion. In August 2025, a case described the kidnapping and detention of a former crypto trader between Paris and Saint-Germain-en-Laye.
In September 2025, media covered a young Swiss person kidnapped in France, with ransom demanded in cryptocurrencies and violence against the victim; in December 2025, the abduction of an entrepreneur’s father in Val-d’Oise, with a possible crypto link discussed in the background; a Charente-Maritime home invasion where attackers forced the transfer of crypto-assets worth several million euros without moving the victims. Already in 2026 describes attackers holding a woman at home while searching for a USB device linked to her partner’s cryptocurrencies.
There are more incidents of this nature. Inevitably, the list is growing.
How to protect yourself?
Protection has two layers. The first is reducing the risk of being “tracked down” - someone learning that a user holds significant crypto assets and linking that to a real-world identity or location. The second is setting up storage so that a rapid, forced transfer is difficult or impossible. A third layer is physical security, but it is not covered here.
Limiting tracking
The French Interior Ministry itself recommends reducing exposure on the internet and in private life. That means avoiding public statements or hints about holding crypto, avoiding real-time posts from industry events (even avoiding appearing at such industry conferences?), using separate email addresses and phone numbers for crypto services, and having hardware shipped to an address not linked to the home address (for example a PO box, a pickup point, or a workplace address).
Storage setup
When crypto is held in self-custody, a single person with the key or seed can often move funds immediately. That is why these attacks tend to focus on forcing an on-the-spot transfer.
Two technical setups can slow that down.
A time lock adds a waiting period, so a transfer cannot go through until enough time has passed, even if access is forced.
A multisignature wallet scheme (multisig) requires more than one key. For instance, in a “2 of 3” setup, two separate keys are needed to move funds. If one key is at home while another is kept elsewhere or held by a trusted person, a single attack in one location may not be enough to complete the transfer right away.
A common approach is to keep only a small amount in a “hot” wallet for everyday spending, and place the rest behind a time lock or multisig. Keys and recovery phrases are stored separately, with some kept outside the home. The recovery phrase is not stored online.
Physical security
After the series of kidnappings, the French Interior Ministry launched a process for the industry. They include home security consultations, briefings for higher-risk individuals, and priority access to the emergency number.
These steps can make it harder to drain all holdings quickly during a single attack, but they do not remove the risk of violence. Defending against a “wrench attack” remains difficult, especially when someone is easy to identify as a target because their connection to crypto and their lifestyle are publicly visible.