TechLetters Insights - Ukraine report highlighting the links between kinetic warfare and cyberattacks - is a new definition of aggression needed
Not really.
Ukraine's assessment of Russian cyberwarfare activity during the current war is a highly interesting document. It highlights coordination between cyber and kinetic attacks. Even if the link as presented seems circumstantial, and no particularly direct linkage is apparently shown, it is nonetheless an important observation. This document may well be among the most important cybersecurity-related assessments released this year (considering the relevance, importance, perhaps impact), and it’s only January as of yet.
This post holds value for cyberpolicy, cyberwarfare considerations, but also cyber threat intelligence (if only for how to communicate observations), the importance of which now is crucial.
Good job
I commend the government of Ukraine for dealing with such an important study and assessment. Oddly, the assessment does not mention the activities that I highlight as the likely prelude points to the war forward
Oddly, as it would be quite easy to measure its impact technically and legally.
The assessment
Here comes its partial assessment. I reference just the most important aspects. The document itself in its ‘motivation part’ is mostly citing stuff that is already public, to arrive at some conclusions/recommendations. One thing stands out.
Cyberattacks are not attacks
This document strives to be on a strict topic, with recommendations for international law. So let’s be strict. That’s actually the most critical part.
“Cyber attacks, like conventional attacks of the Russian Federation, do not recognize any rules - infrastructure, humanitarian organizations, and private and state-owned companies are under attack.”
Unfortunately, the document misunderstand the notion of “cyberattack”, assuming that they always equal “attacks” in the international law sense. This is not to the case. Attacks which are defined as acts of violence in defense or offense. So typically would involve actual hostilities, acts such as high-impact destruction of objects/property or causing killings/injuries. It is clear that not many, if not none at all, cyberattacks, ever attain such a level. Therefore, such a classification is not correct. No digital infrastructure was subjected to an "attack" checking the box of international law-grade events. Cyberattacks are not attacks, at least almost never. Sorry, but that's the existing framework that we have. That's one particular major misunderstanding of international law in this work. It is curious that authors are unaware.
It is also unclear to what extent the following presumption is drawn on merit:
“Powerful cyber attacks can be used as compensators for conventional warfare failures”.
Since (as is also mentioned in this report), no particularly “powerful” cyberattacks, or at least out-of-ordinary events, are highlighted (unless of course the KA-SAT satellite communication infrastructure). What is the “powerful” here? Just coinciding with war? OK… But surely we cannot classify just about any random cyber event as a “powerful cyberattack”? And the particular one references close to the quoted sentence (a failed attempt to hack parts of the energy grid) was not powerful — as it did not happen (it was also never revealed in public what could be the actual effects, should it happen; someone should know this by now, right?). International law deals with effects.
However, this presumption offers a clearly correct, and important message: “An aggressor state can combine conventional and cyber attacks to increase panic attacks among the civilian population”.
War crimes?
That said, it isn’t clear if enough evidence is shown for: “War crimes can be committed both conventionally and in cyberspace”. Specifically, which events listed are the “war crimes” in view of the authors? As the report highlights, the cyberattack in question on energy facilities did not succeed (fortunately), and war crime is a post-factual aspect. War crime is a particularly legal term, just saying.
Cyber United Nations…
The report then concludes that a ‘Cyber United Nations’ should be created and that the United Nations should update the definition of ‘aggression’ to include cyberattacks. First, reasonably reasoning, most of the presented initial preface should be seen as forming only slight background for advancing such suggestions, as the presented events are not of significant cyber operations that the world at large was unaware of. That said, one thing is to imagine things to come, and another to actually see them. And indeed we’re seeing the first full-scale armed conflict with a cyberwarfare component (accompanying air, sea, and land operations).
However, in other words, nothing standing ‘out of ordinary’ is demonstrated to formulate such bold proposals. Do we need an ‘Air United Nations’ (a United Nations for air activities)? Well, we do have the International Civil Aviation Organisation (civilian!). True. So one could then argue that we already have the International Telecommunication Union? Otherwise, the UN does not deal with direct warfare operations, aside from the Security Council, maybe…
Thus, the suggestion for ‘cyber united nations’ and the modification of the definition of aggression can be understood as put forward without necessarily being grounded in the initial part of the report (which risks suggesting that the two parts are disconnected). In what ways the Cyber United Nations would help at all? This is not explained. But I don’t necessarily see a problem here. States are free to put forward any ideas to consider.
Cyber as aggression
Also of note, I stress that the modernisation of the definition of aggression in the United Nations General Assembly resolution 3314 (XXIX) is a good idea anyway!
It should consider cyberattacks more directly. We must consider, however, that the definition of aggression was 'found' based on the existing knowledge of existing international law. It was not in fact 'defined' or ‘decreed’. It did not come ‘out of vacuum’.
How is aggression defined?
“
(a) The invasion or attack by the armed forces of a State of the territory of another State, or any military occupation, however temporary, resulting from such invasion or attack, or any annexation by the use of force of the territory of another State or part thereof,
(b) Bombardment by the armed forces of a State against the territory of another State or the use of any weapons by a State against the territory of another State;
(c) The blockade of the ports or coasts of a State by the armed forces of another State;
(d) An attack by the armed forces of a State on the land, sea, or air forces, or marine and air fleets of another State;
(e) The use of armed forces of one State which are within the territory of another State with the agreement of the receiving State, in contravention of the conditions provided for in the agreement or any extension of their presence in such territory beyond the termination of the agreement;
(f) The action of a State in allowing its territory, which it has placed at the disposal of another State, to be used by that other State for perpetrating an act of aggression against a third State;
(g) The sending by or on behalf of a State of armed bands, groups, irregulars or mercenaries, which carry out acts of armed force against another State of such gravity as to amount to the acts listed above, or its substantial involvement therein.
“
It is clear that some of the above is happening in the Ukraine war. To conclude that such activities constitute aggression, no formal definition was needed.
Cyberattack as aggression?
Therefore, the report goes, it is to be identified that cyberattacks may constitute aggression. To be widely acceptable, such a designation would also have to be based on existing international law norms, e.g. the one I reference at the beginning of this article. Such understanding is now being built gradually, even if not formally codified by a UN resolution (which I do not exclude in the future)
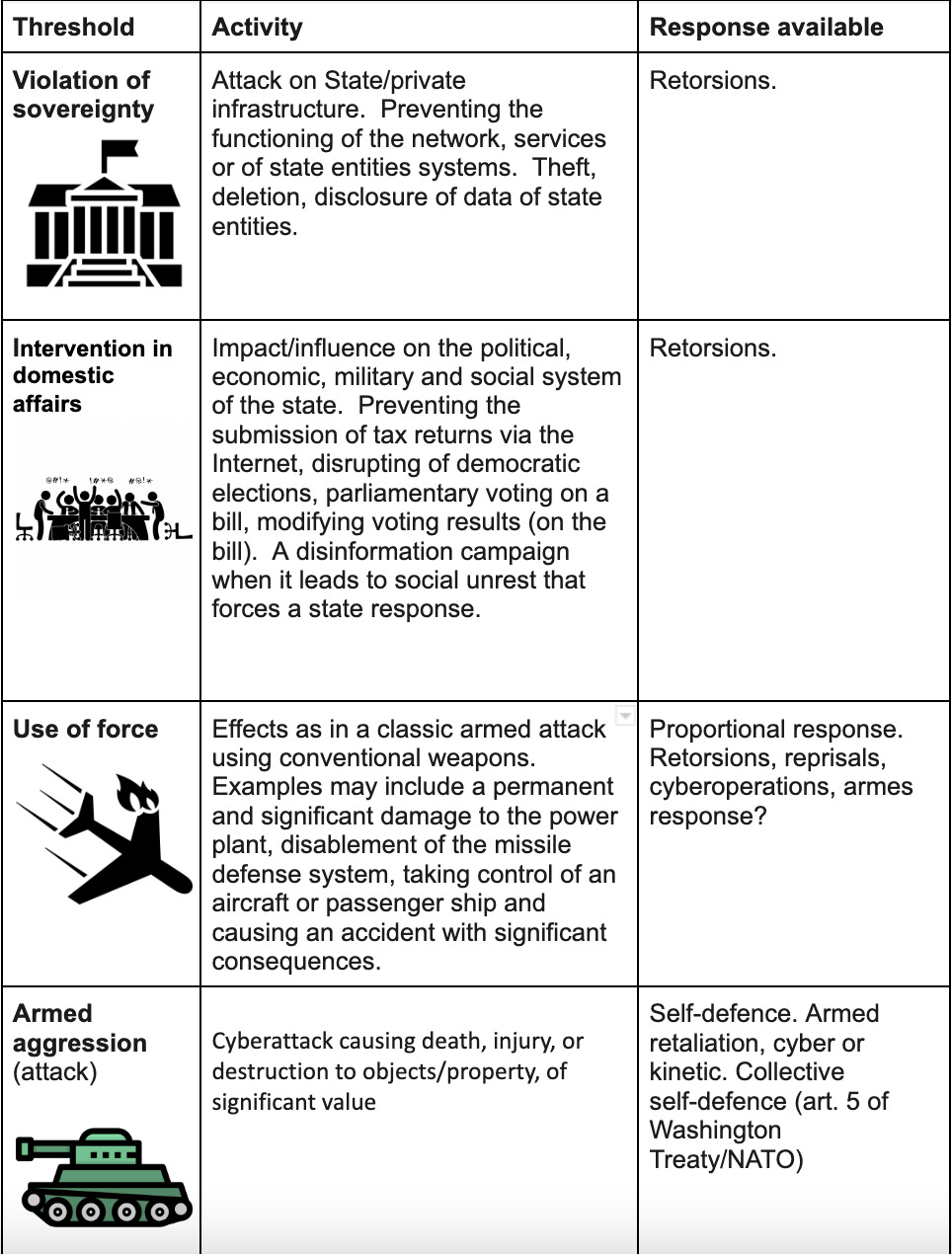
For now, the most reasonable way is to assume that cyberattacks can constitute aggression, as they really can. Many countries already stated this. See this impact assessment grade of cyberattacks:
So it’s not exactly controversial or unknown by now.
If a significant enough cyberattack happens, which is measured by its effects, it can well be perceived as aggression. It does not need to be defined as such. That said, I understand the push of Ukraine for this international cybersecurity proposal. As I said, such a definition should be updated, eventually. We did not have to have a full-scale war to know it.
But Ukraine’s document stating that “the legal definition of aggression was formulated” is imprecise. The “definition” was not “just formulated”. It was made concrete based on existing rules. This should be appreciated - definitions do not magically come out of the vacuum. This sentence may highlight what this proposal is really about: “Unfortunately, international law also almost completely ignores the concept of economic aggression”. Indeed.
Do Laws of War need to change?
Now that is an interesting can of worms: “international humanitarian law should become more predictive and offer adequate regulation of the relevant legal relations”. Indeed, international humanitarian law (also known as the law of armed conflict) ‘regulates’ the conduct of hostilities and puts limits to protect civilians. Countries currently debate how it may relate to cyberwarfare. But so far it is understood that it would be extremely difficult to find a State agreement to tighten the framework. Perhaps a better avenue is to reinterpret its rules to arrive at new norms.
In summary - it is an important milestone of 2023
The document highlights the continual importance of cybersecurity as a technology and policy issue, even international security. It is undeniable that the current cyberwar will have consequences for years or even decades to come. How the changes would be shaped is another issue. The document is interesting food for thought, even if the cases listed sometimes appear to be decoupled from the final conclusions.
This highlights the need for strict reasoning and analysis to guarantee that communication and conclusive parts remain connected. It is of consideration for cyber policy, but also for cyber threat intelligence.
Did you like the assessment and analysis? Any questions, comments, complaints, or offers of engagement ? Feel free to reach out: me@lukaszolejnik.com