TechLetters ☕️ Trump's revamp of US cyber. China accuses US of cyberattacks. Migration to quantum-safe systems. Privacy risks at a scale are larger than expected. Quantum computer factorised 35.
My analysis of the future Trump approach to cyber domain. Cybersecurity will be transformed, aiming to integrate it with electronic warfare (EW). It's not just about defense; it's a shift in how conflicts are conducted. Importance to draw conclusions from the war in Ukraine: Cyber shaped the info space pre-war, supported military ops during conflict, and will persist post-war. But will the potential future U.S. conflicts look like Russian war in Ukraine?
https://techletters.substack.com/p/techletters-insights-trumps-plans
Security
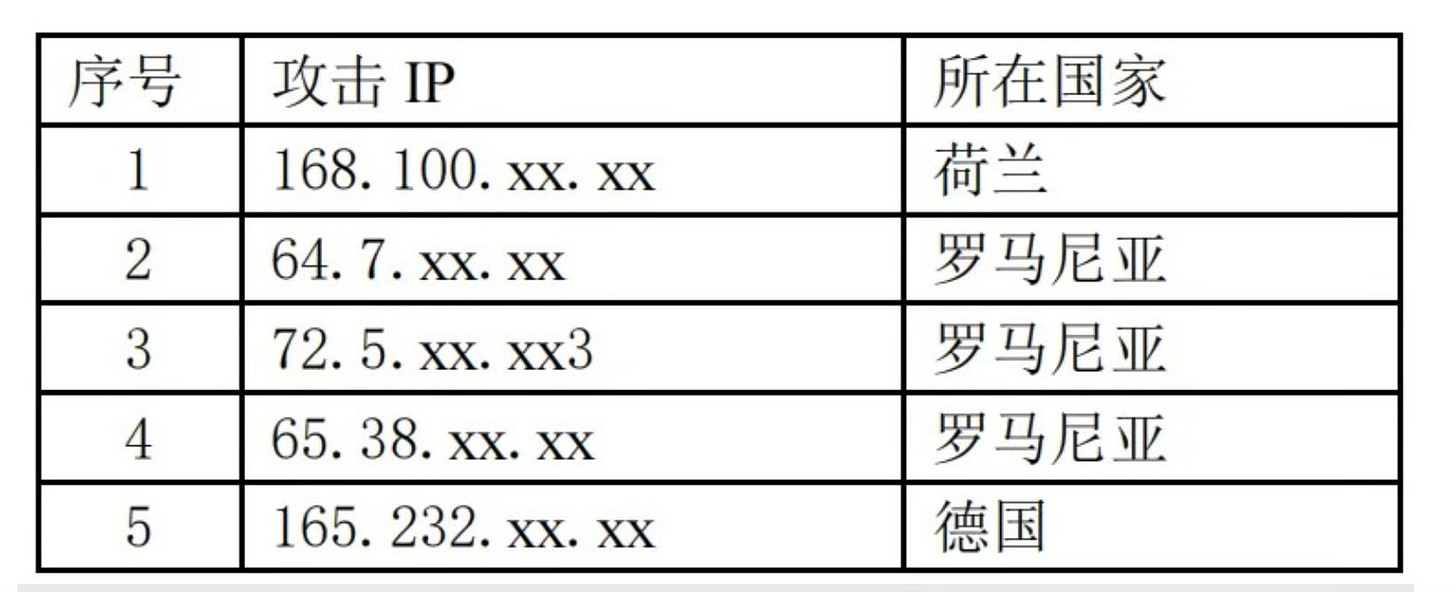
China's Ministry of Foreign Affairs has accused the U.S. of conducting long-term, systematic, and large-scale cyberattacks against China. An unprecedentedly strong lines from the Chinese government. Reports indicate that China and the U.S. are engaged in negotiations regarding cyberattacks. Chinese sources suggest the scope of U.S. cyber operations has exceeded traditional espionage, a serious accusation, and seems to be a symmetric text response to what was being released in the U.S. media about China’s activities (Volt Typhoon, etc). This follows the release of a report by China’s cybersecurity authority, which claims to provide technical evidence of such attacks, though details are small. No information about how the alleged compromise happened. The table below reportedly lists proxies and Indicators of Compromis.: https://app.xinhuanet.com/news/article.html?articleId=b301c226b63ded0d52e2f5a74c74142c.
Migrating to quantum-resistant systems. Cryptography Suite 2.0 is designed to safeguard against potential quantum computer attacks, irrespective of when they may occur—15, 100, or 500 years from now. While data encrypted with weaker algorithms might eventually be decrypted, its future value is expected to be negligible. The National Security Agency (NSA) emphasizes the need for proactive measures due to significant progress in quantum computing research, despite uncertainty about the arrival of a Cryptographically Relevant Quantum Computer (CRQC). This necessitates immediate action to ensure secure systems. Quantum cryptography is deemed impractical, not secure for practical deployments, and is not recommended. Similarly, hybrid cryptographic solutions are discouraged due to their added complexity, which introduces interoperability issues, complicates testing, and requires dual transitions. Most security failures result from these implementation flaws rather than weaknesses in cryptographic algorithms. https://media.defense.gov/2022/Sep/07/2003071836/-1/-1/0/CSI_CNSA_2.0_FAQ_.PDF
Party like it’s 25 years ago. 6 vulnerabilities in rsync. In the most severe CVE, an attacker only requires anonymous read access to a rsync server, such as a public mirror, to execute arbitrary code on the machine the server is running on. https://www.openwall.com/lists/oss-security/2025/01/14/3
International team (USA & France) used active operations to remove PlugX malware from thousands computers around the world. L’opération de cyber-désinfection. French law enforcement agency has gained access to the command & control server. This server sent commands to computers infected with the variant of PlugX malware to issue a command causing self-destruct. https://www.tribunal-de-paris.justice.fr/sites/default/files/2024-07/2024-07-24%20-%20CP%20d%C3%A9mant%C3%A8lement%20botnet%20d%27espionnage%20plugX.pdf https://www.justice.gov/opa/media/1384136/dl
Privacy
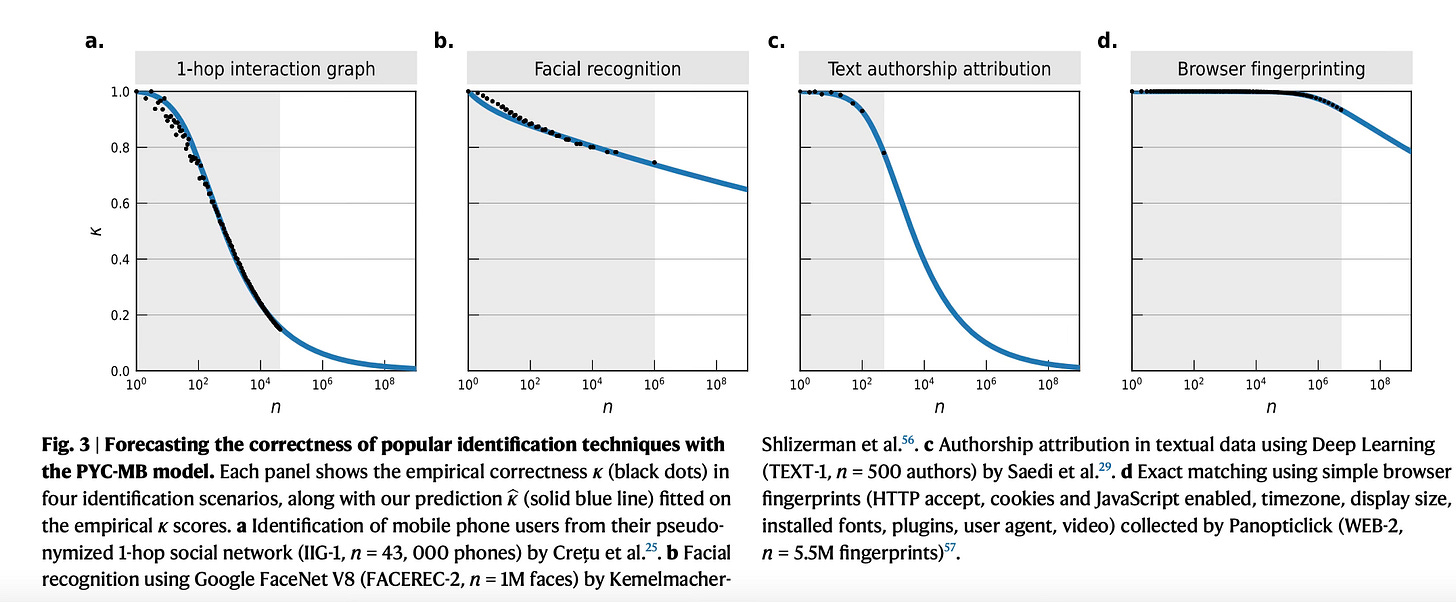
How easy is it to identify users, and does the increasing capability of AI challenge our current understanding of privacy and anonymity? Facial recognition systems can identify 62% of individuals globally, while browser fingerprinting achieves 75% accuracy among 4 billion devices. https://www.nature.com/articles/s41467-024-55296-6
The Berlin Group report on data protection aspects of large language models/AI. Interesting but seems somewhat outdated, as it does not address the growing capability of LLMs to use tools or APIs. It repeats the cliché that "LLMs facilitate a higher volume of persuasive disinformation generation that can then be spread easily, cheaply, and at a much higher speed." However, the report fails to address the "spread" aspect in detail, let alone the claims of "cheaply" or "at much higher speed," which are not dependent on LLMs themselves. It also mentions multiple examples of LLMs "spreading" misinformation but provides no concrete instances. Do you know of any case where an LLM directly caused such spread? However, I fully agree with the Berlin Group's view that running LLMs locally is superior for privacy and data protection. I don’t think memory or processing constraints will be a barrier for long. Soon, it will be common for everyone to have multiple LLMs running locally on their devices.
Other
Primer on integer factorisation using quantum methods. So far only small integers N ≤ 35 were successfully factored on demonstrators. Analog quantum computing device factored 23-bit integer 8219999 on a a D-Wave quantum annealer. Simulators factored 39-bit number 549755813701. Long road before quantum computers break any ciphers https://arxiv.org/abs/2410.14397
In case you feel it's worth it to forward this content further:
Subscribed
If you’d like to share: