TechLetters #12 - Covid health passports hurdles; hacking EMA, sudo, or security researchers; privacy-preserving advertising systems?
Éditorial
Two vulnerabilities that matter emerged this week.
And slowly - one piece of applications, soon gaining popularity and tractions. Covid Passports?
I provide an assessment-analysis concerning covid health/sanitary passport/certificates. A lot of people devoted (perhaps too) much time to the niche technology of digital contact tracing. But it seems that health passports, touted since Spring 2020, are getting State traction. I explain how to think about this thing. It concerns sensitive matters, this goes beyond personal data.
It’s about privacy but also proportionality and generally regulating life with technology. In principle, it is possible to decrease the invasiveness, guaranteeing that personal data are processed to the minimum. But this requires care. Is anyone interested, even?
Security
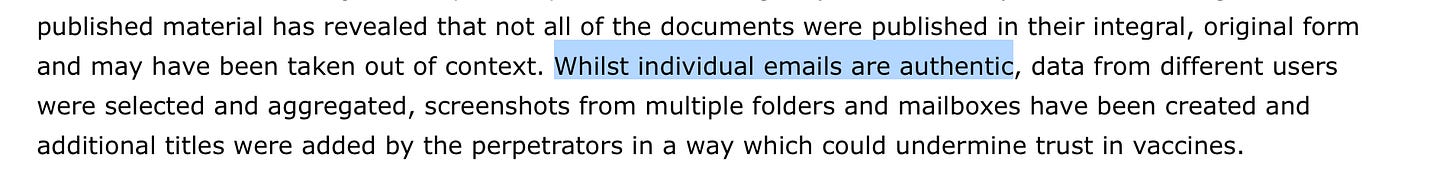
EMA hack. Update to the hack-and-leak compromise of the European Medicines Agency. Confirms that the content of communication/documents is essentially not tampered with - the information operation is taking advantage of a selective release, as I said before. This means that someone may have betted on the difficulty to understand these documents anyway.
Hacking security researchers? North Korea government hacking group attempted to hack cybersecurity researchers. "observed targeting specific security researchers". Tainted Visual Studio project in use (containing malware). Waterhole website set ("researchers have been compromised after visiting the actors’ blog"). They attacked security researchers specifically. While reasons are not known, perhaps they were after information or desired to access to working exploits? I can imagine many others are targeted with such attempted communication. In fact, I am sure many in security circles may have received similarly suspicious communication of the kind over the previous years…
Sudo bug. Buffer overflow found in sudo, a very popular binary on Linux/Unix systems. Many systems at risk of getting hacked. "Any unprivileged user can gain root privileges". 10-year old bug. Here’s the exploit.
Libgcrypt bug. A security vulnerability is a widely used cryptographic library. Really serious stuff. Systems can be hacked. Data made unsafe, etc. "update immediately to version 1.9.1".
EMOTET, down. The malware has been disrupted by the global action of law enforcement.
Privacy
Ads Technology, privacy? Google provides an update to their Privacy Sandbox experiment. Some features in testing mode were deployed to Chrome browser in March/April. Conceptually at least, privacy-proofed ads systems are possible, just difficult and requiring business decisions. 2021 will be an eventful year, with web standards at the center. To a former W3C TAG member and a researcher with long-term involvement of standards privacy engineering research, this surely is curious.
Data, stop. Italian Data Protection Authority issued an order compelling TikTok to "stop processing data", in the case of users of unknown age (with “full certainty” - users should be min 13-years-old). "immediate effect from the date of receipt". GDPR precedent.
Other
Catchy GPS. Military tests of GPS impact on the use in professional civilian settings.
Previously undisclosed Federal Aviation Administration (FAA) data for a few months in 2017 and 2018 detail hundreds of aircraft losing GPS reception in the vicinity of military tests
…
“To say that my raw data navigation skills were lacking is an understatement! I’ve never done it on the Airbus and can’t remember having done it in 25 years or more.”
Military drills with a technology widely-used for civilian purposes. What can go wrong?
That’s it this time, thanks!
In case you feel it's worth it to forward this letter further, I leave this thingy below: